Real-Time Third-Party Cyber Risk Management for Your Supply Chain
Take control of your vendor ecosystem with unrivaled security data and risk intelligence. Continuously monitor third-party risk, identify vulnerabilities, and work with vendors to remediate critical issues – all in one platform.
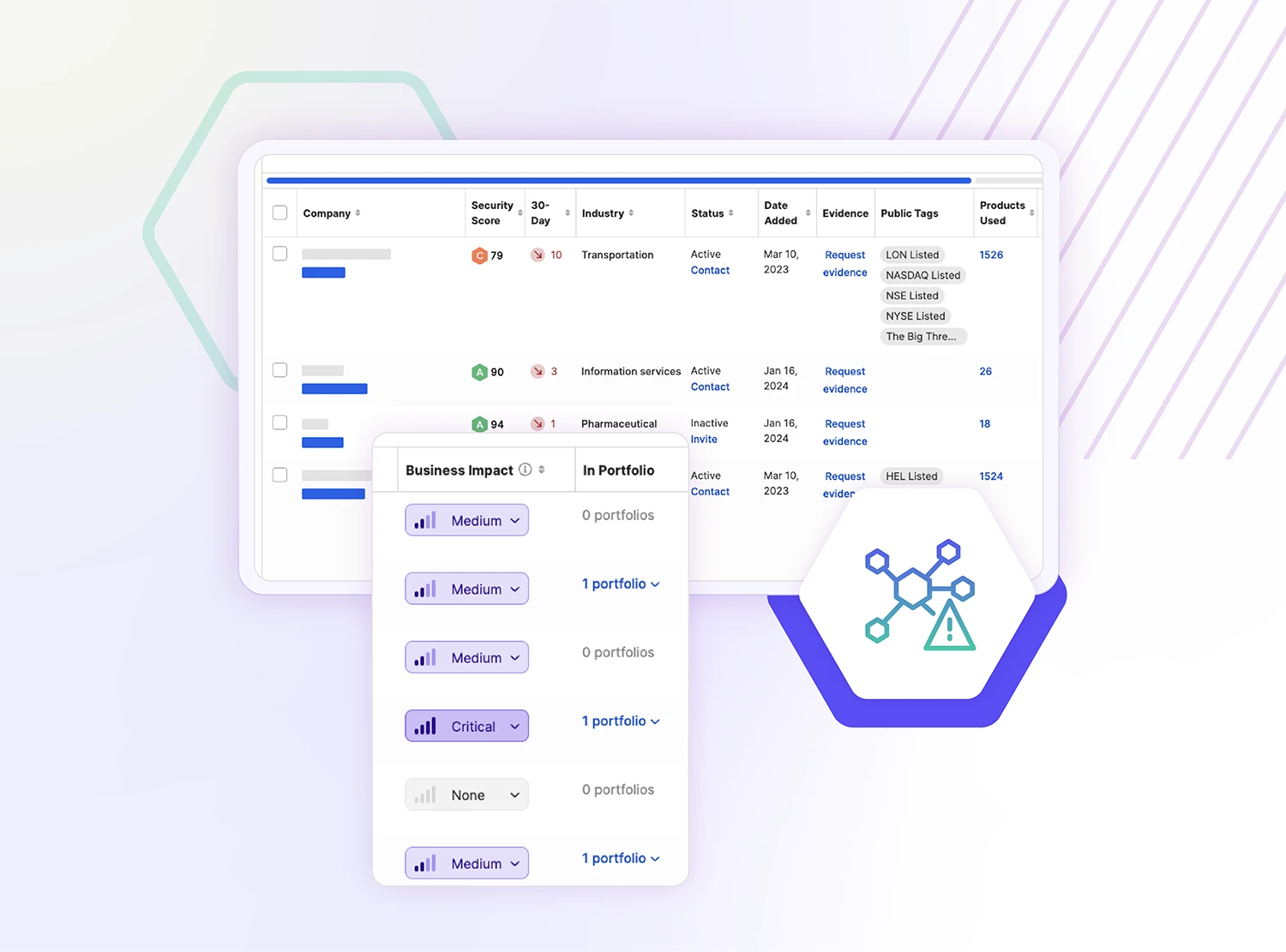
Instantly understand the cyber risk of any third-party
Ninety-eight percent of organizations are connected to at least one vendor that’s had a breach in the last two years. As the global attack surface continues to expand, security and vendor risk management teams need complete visibility into their entire supply chain.
Automate your third-party risk management workflows, uncover hidden vulnerabilities, and collaborate with your partners to build a secure supply chain.
Reduce risk to your business
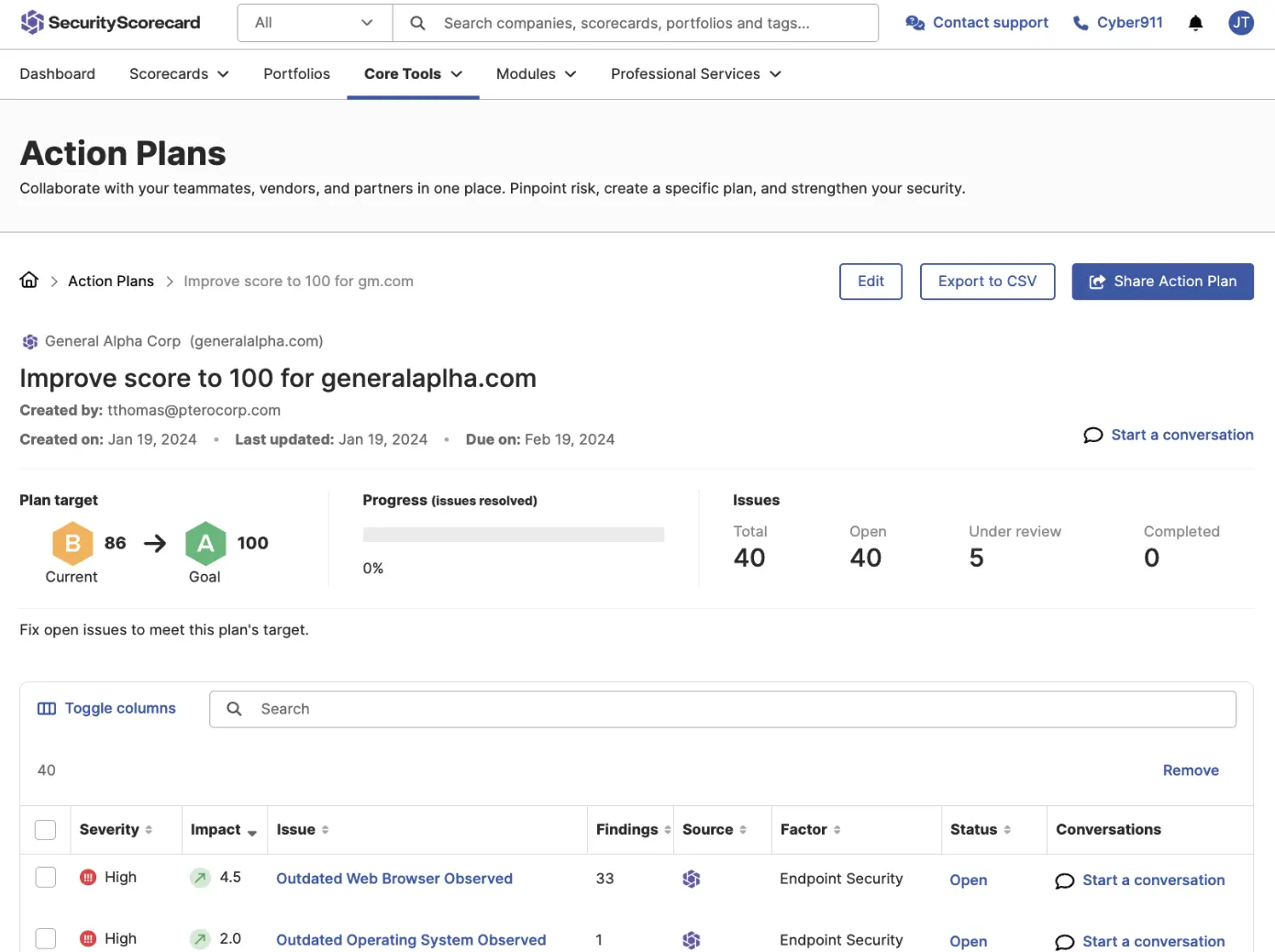
Score and Action Plans
Streamline collaboration with internal stakeholders and their third-parties in one dashboard, and create plans for your vendors to improve their security posture
Generate dynamic remediation plans
Prioritize critical vulnerabilities and assign individuals to fix issues
See progress in real time, saving hours and reducing ecosystem risk. Eliminate email back and forths, manual spreadsheets
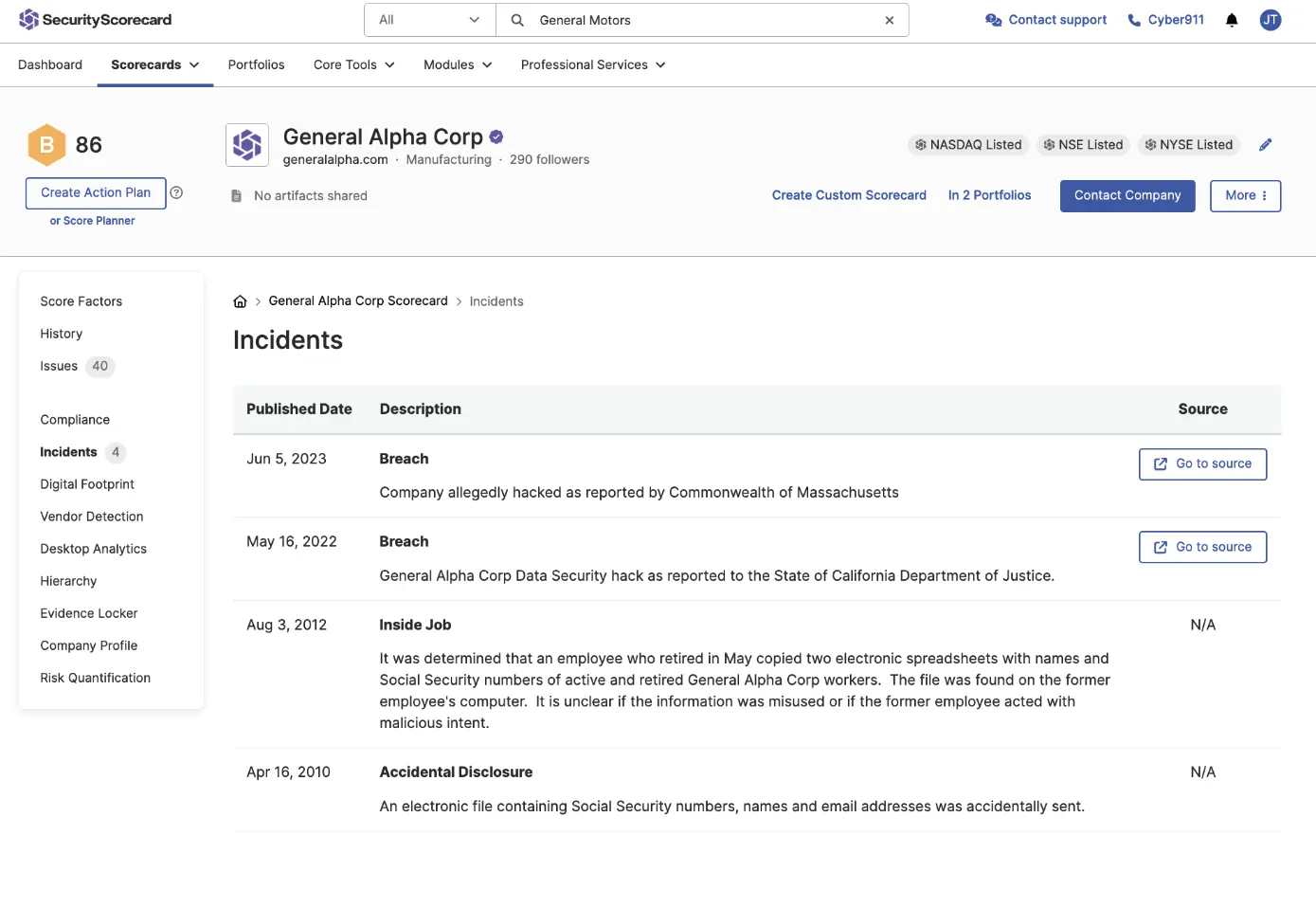
Incidents and Breaches
Continuously monitor and assess your third-parties with breach and incident data to ensure compliance and safeguard your supply chain against potential cyber threats.
Proactively mitigate risk and stay ahead of threats with real-time notifications of third-party breaches and incidents
Get detailed insights into security incidents across your vendor ecosystem to better prioritize responses and enhance your third-party risk management strategy
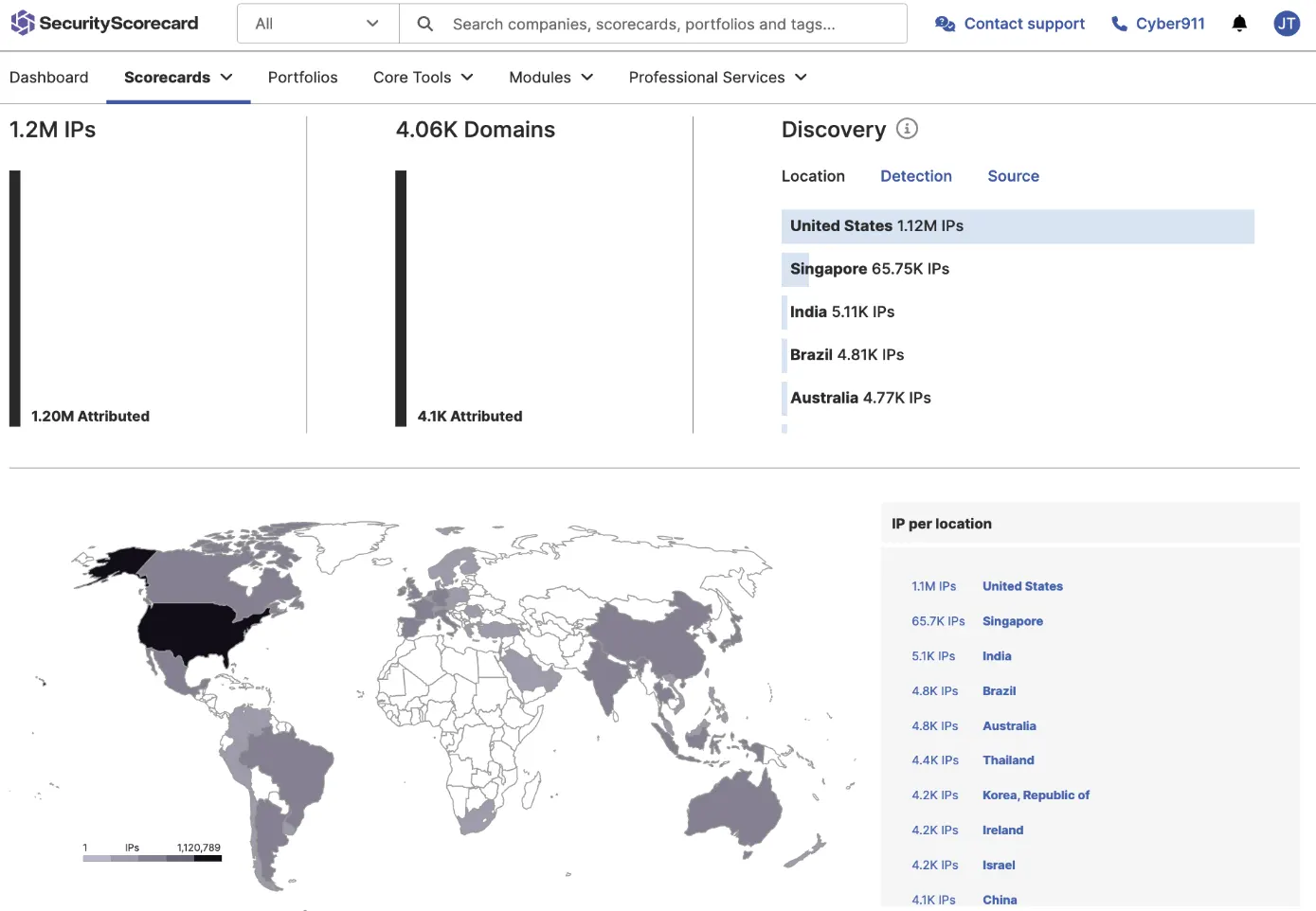
Digital Footprint
See the full picture of external attack surface for your supply chain, including potential vulnerabilities that hackers could exploit
Leverage real-time monitoring to proactively identify risks
Prioritize risk by identifying which parts of the attack surface pose the greatest threat
Initiate remediation for specific assets. Focus remediation efforts on the most vulnerable areas of your supply chain, and act before they can be exploited by malicious actors
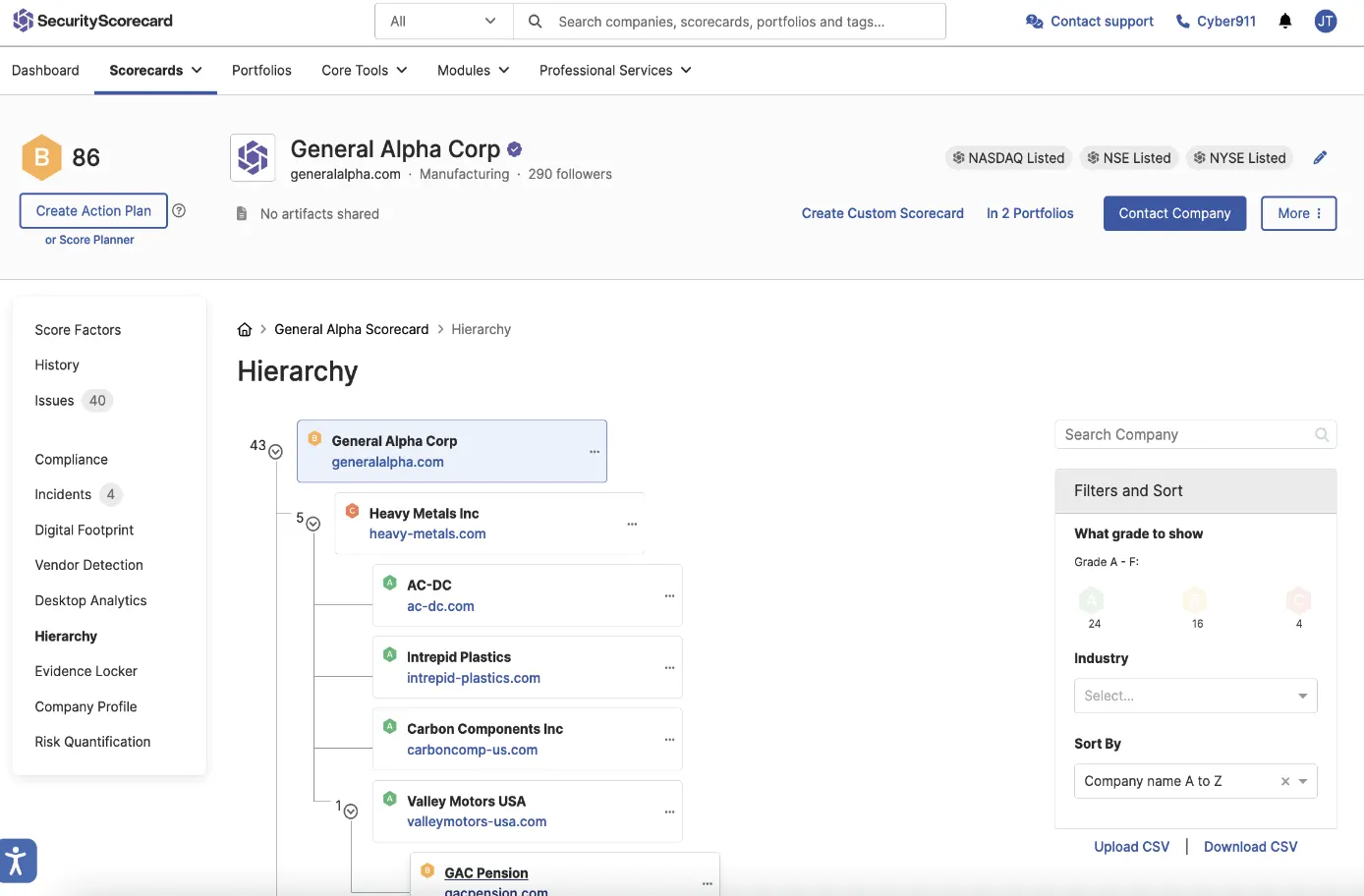
Hierarchy
View the overall risk of your parent organization and their subsidiaries.
Continuously monitor the security posture of your parent organization and its subsidiaries in one hierarchical view.
Understand common risks across your overall entity and quickly prioritize subsidiaries that require additional resources or attention to reduce their cyber risk.
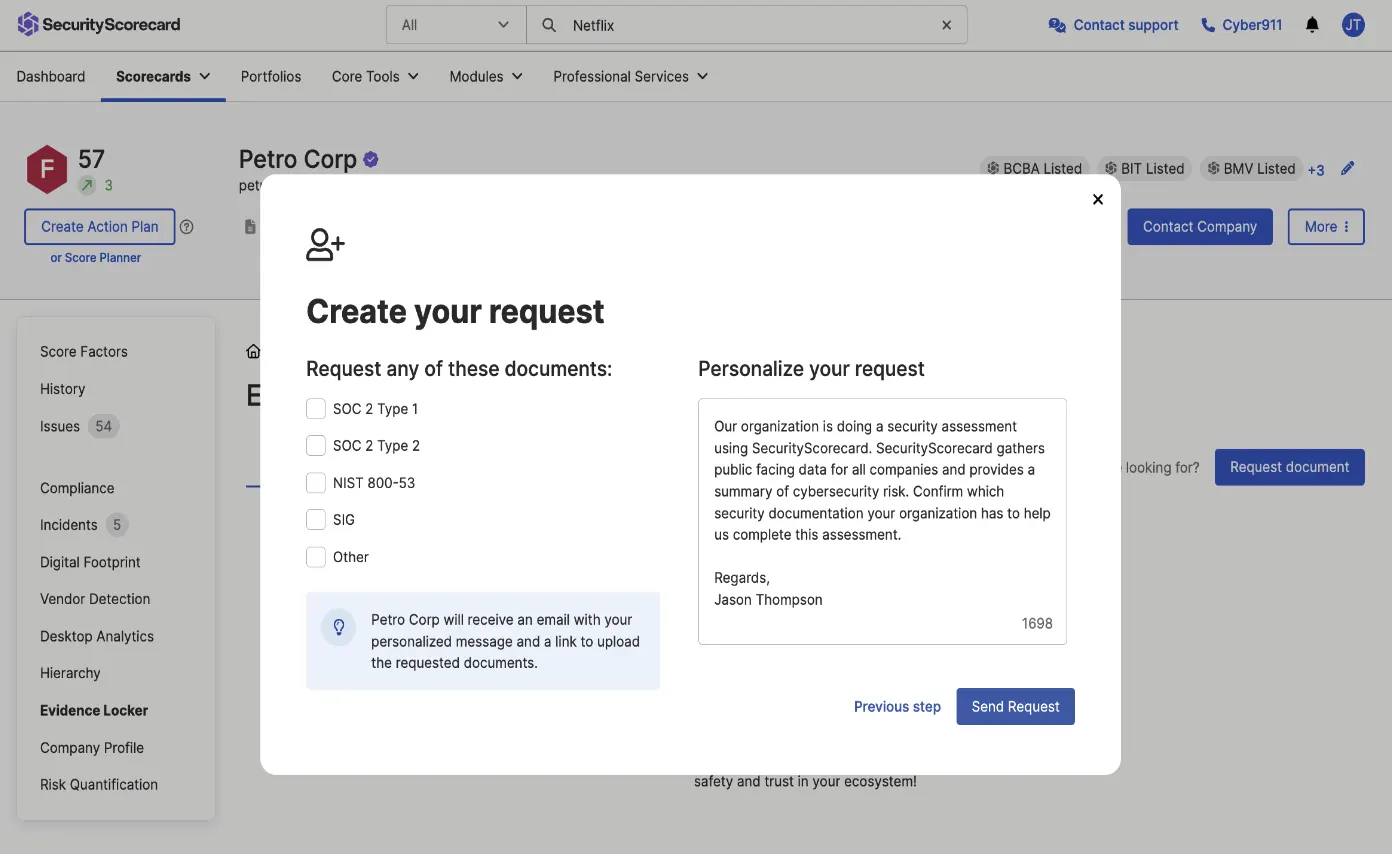
Evidence Locker
Managing compliance evidence is a job in itself. Whether you’re vetting potential vendors, or you are a vendor trying to demonstrate compliance to a prospect, curating multiple files for compliance evidence takes significant time and effort. With SecurityScorecard’s Evidence Locker, you can view and manage these files simply.
Vendor Risk Managers leverage Evidence Locker to quickly vet your vendors’ or potential vendors’ compliance artifacts.
Vendors can showcase their compliance evidence in one place and reduce the time spent sending artifacts to customers and prospects.

