Regulatory Oversight
Prioritize cybersecurity reviews with continuous monitoring to identify who is most at risk.
Prioritize cybersecurity reviews
Scan the global IP space daily to obtain a complete view of your digital ecosystem so you can identify changes that affect your security posture or likelihood of sustaining a breach.
Support breach investigations
Obtain actionable intelligence you can leverage in the event of a breach. This is particularly useful for agencies that don’t receive direct feeds from IC and Law Enforcement
Validate Industry Resilience
Use SecurityScorecard’s outside-in, independent analysis to validate regulatory compliance and improve sector-wide resilience.
Continuously monitor organizations and their security
Regulators can use our data to improve their own organization’s cyberhealth, including their service providers. Using a risk-based approach, regulators are able to quickly see where they should focus.
Image contains redacted material.
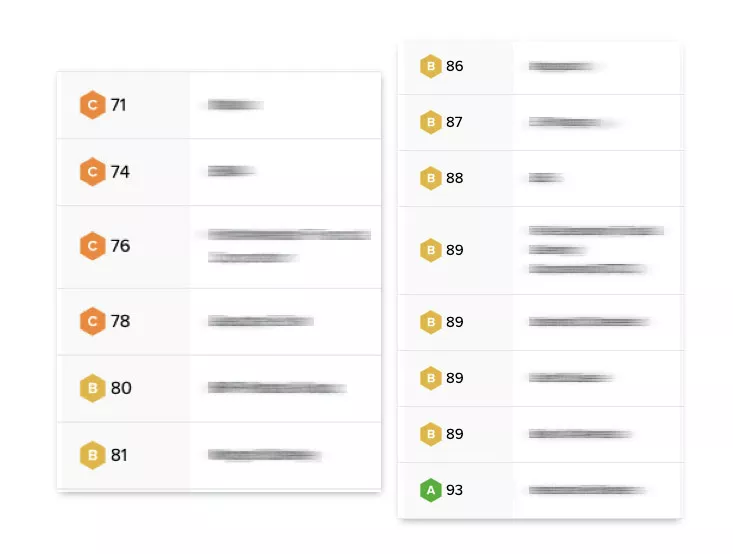
Obtain a complete picture of your cyber risk exposure. Continuously Monitor third-parties’ cybersecurity postures. This provides daily visibility into the health of your cyber ecosystem. If anything seems unusual, you can send questionnaires and communicate with vendors using our internal communication platform (i.e. Atlas).
Image contains redacted material.
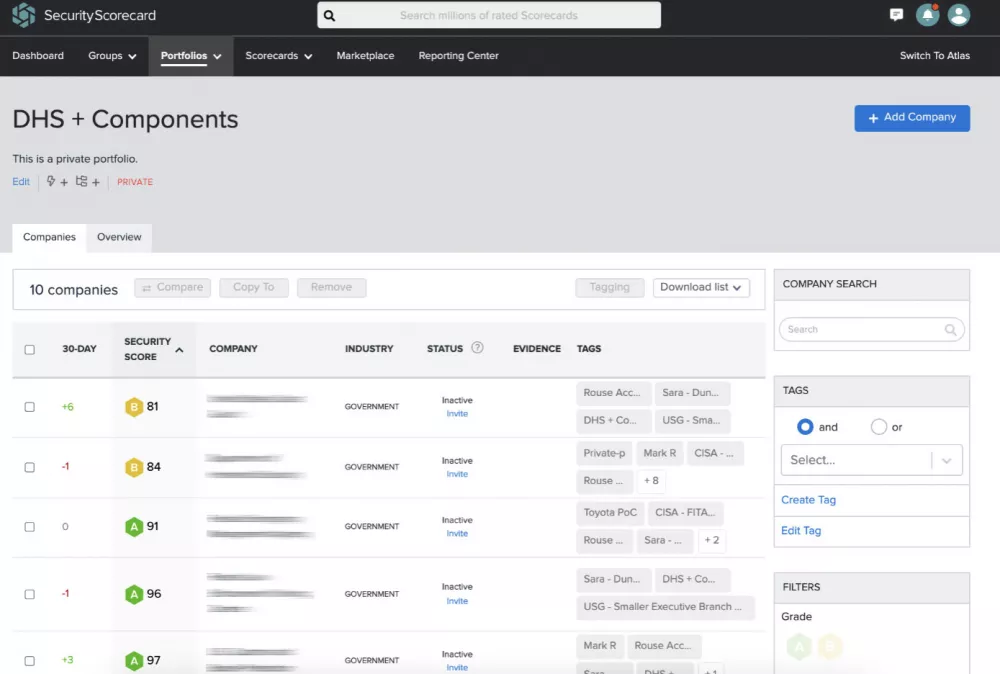
Compare multiple companies’ scores over time. In that historic timeline, identify key events of interest (such as Malware, Ransomware, or a Breach). You can make risk-based procurement decisions as well as share the report link with co-workers.
Image contains redacted material.
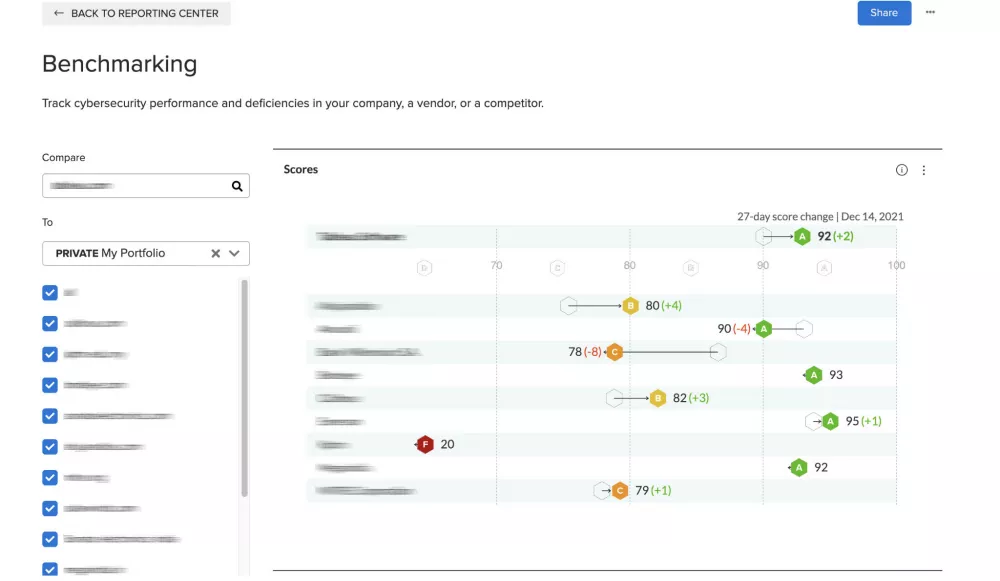
Help agency leaders understand your regulatory posture with intuitive high-level reporting.
Our automated reporting tools and Scorecards make it easy to pull the Ratings and Atlas Questionnaire data you need for security briefings.
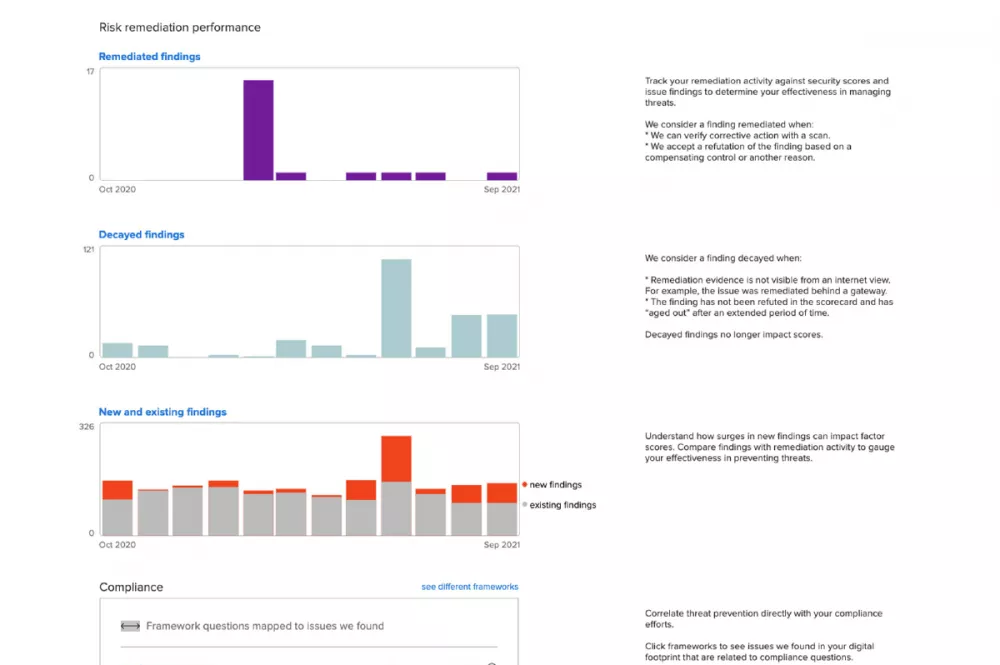
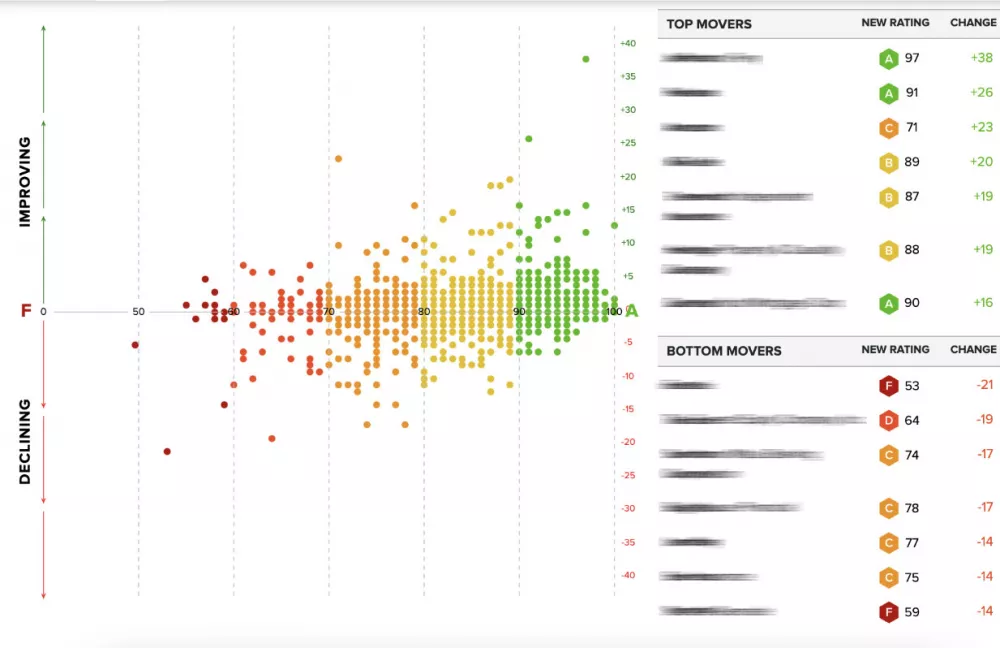
Review the attributed assets of your agency, contractors, and regulated entities. You can easily see which parts of your digital security posture are becoming more likely to be breached (bottom movers). This will help you to identify high-risk assets such as vulnerabilities, unmanaged endpoints, and insecure web domains.
Image contains redacted material.
How Can We Help?
Whether you’re ready to speak someone about pricing, want to dive deeper on a specific topic,
or have a problem that you’re not sure we can address, we’ll contact you with someone who can help.
Head Office
1005 Metropolitan Ave, Corner Kakarong, Makati, 1205 Metro Manila
Cebu Office
2F Unit 202-204, GMC Innovation Center, M. J. Cuenco Ave, Brgy San Roque Cebu City 6000
Davao Office
Unit 11, Plug Holdings Bldg, 141 R. Castillo St, Agdao, Davao City, 8000 Davao del Sur

